Web3 Chain Authentication and Authorization Security Standard (CAA) | International Journal on Recent and Innovation Trends in Computing and Communication
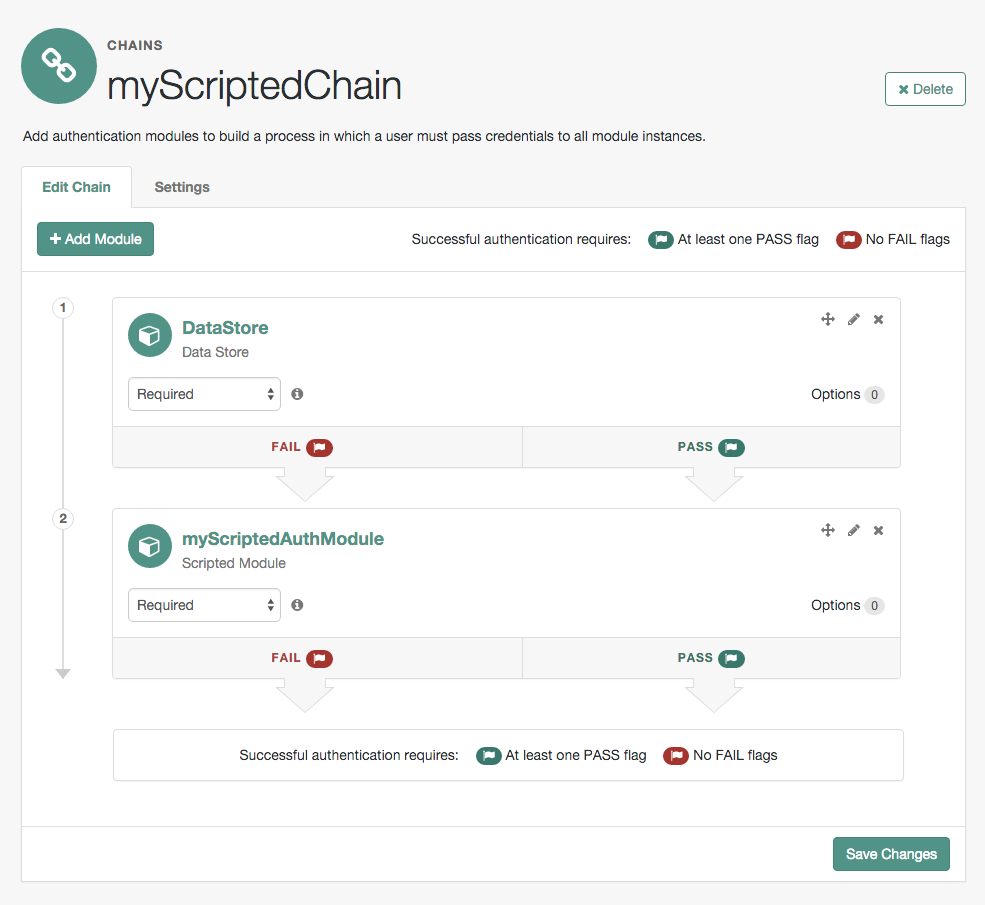
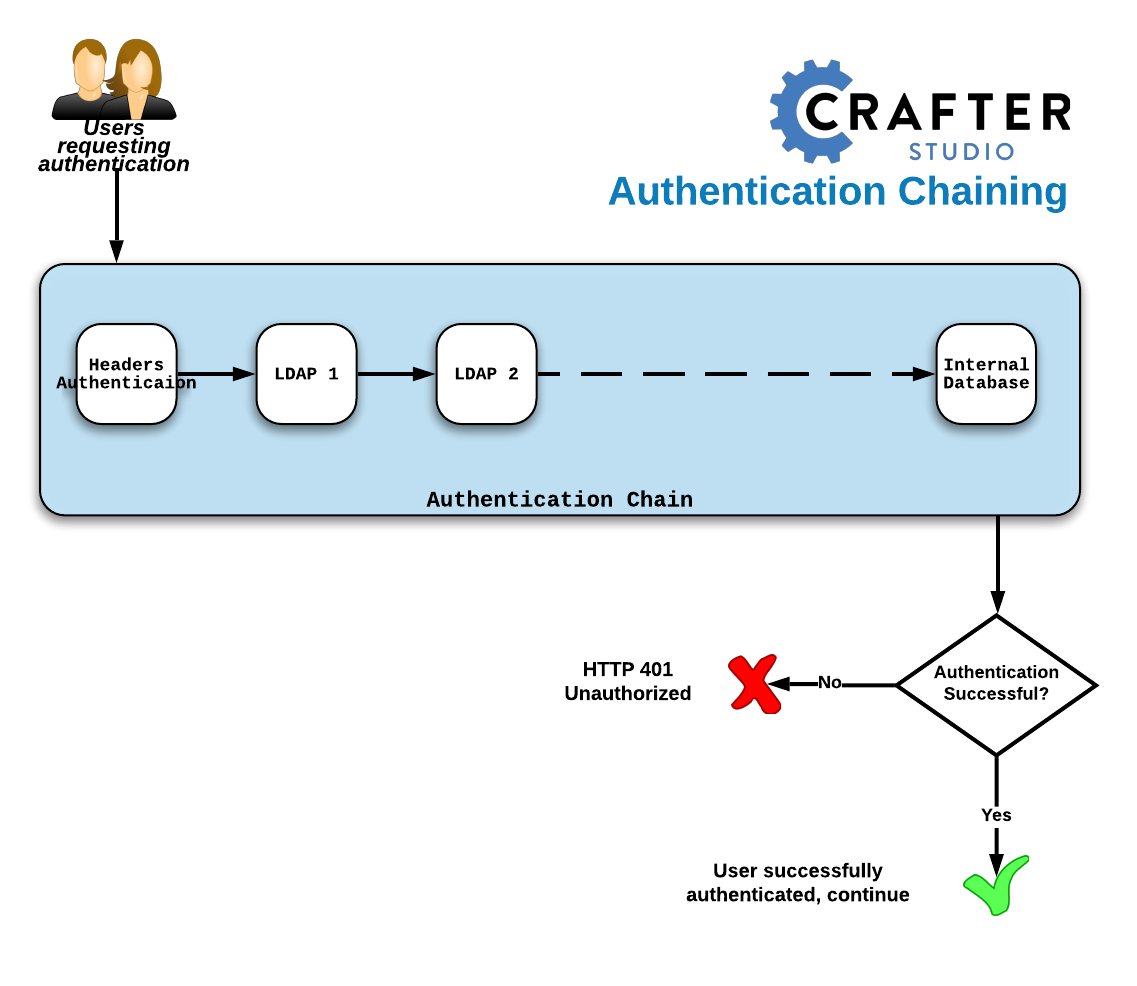
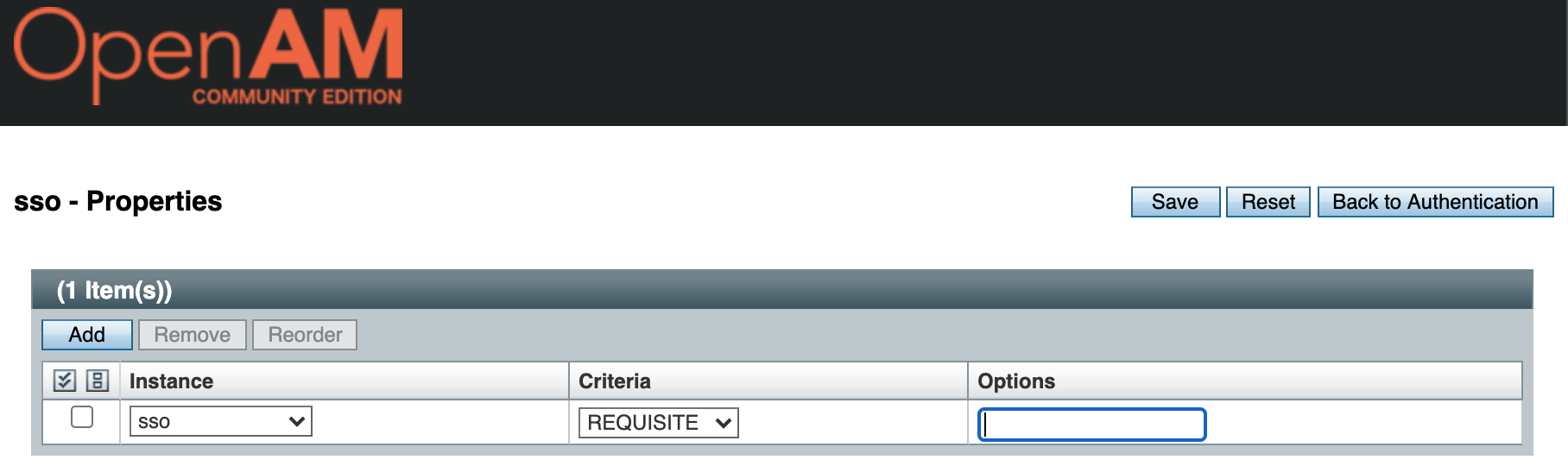
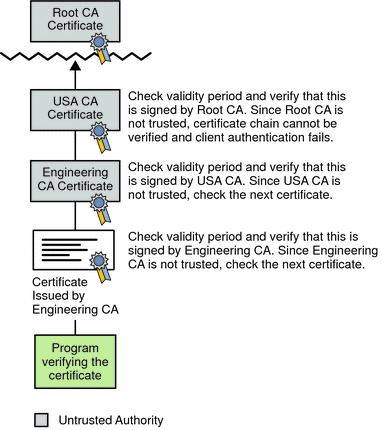
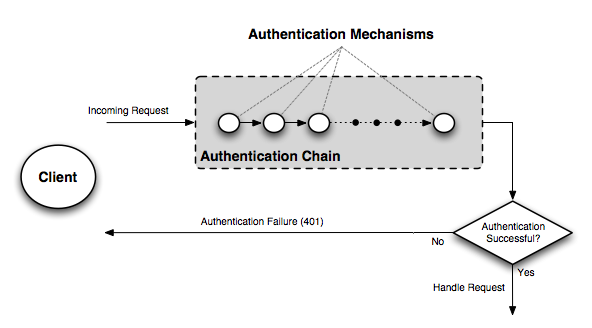
ForgeRock Access Management 7.0.2 > Authentication and Single Sign-On Guide > Authentication Modules and Chains
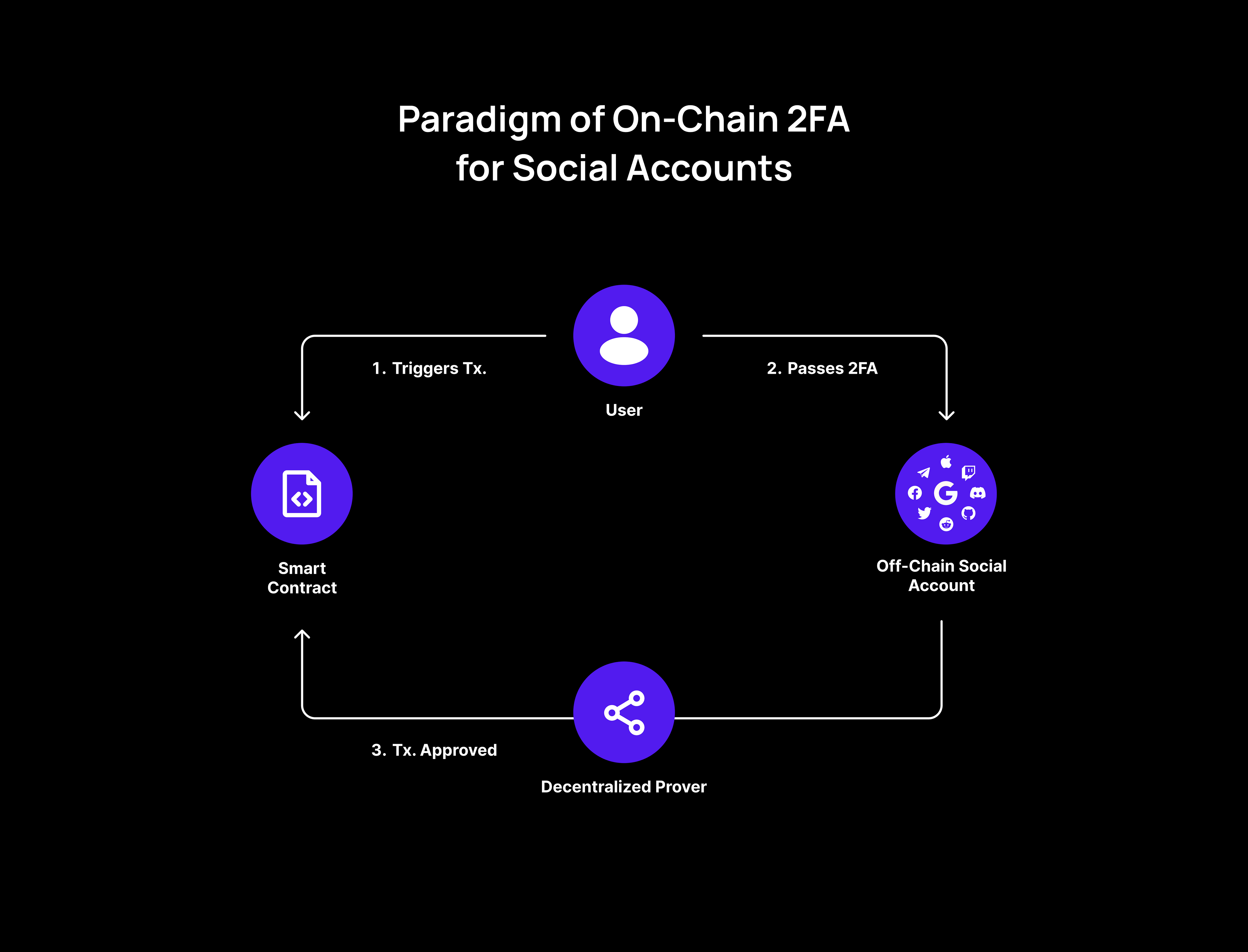
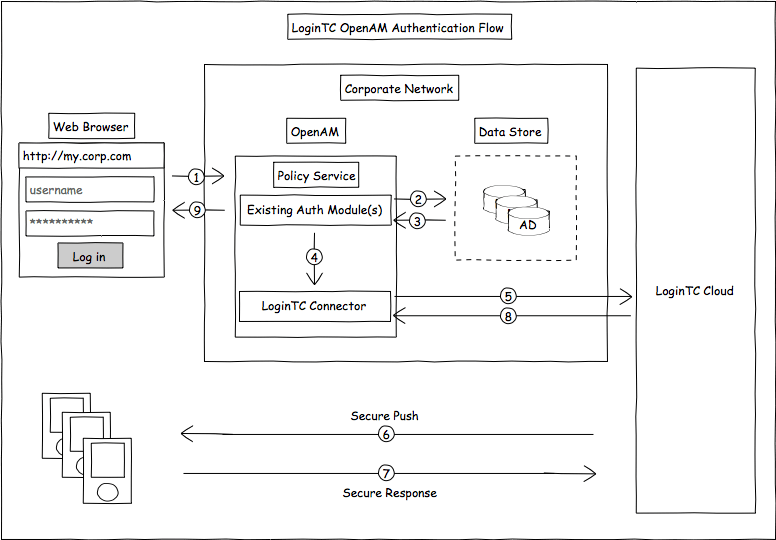
A Proposal of on-chain verifiable Social Identity 2 Factor Authentication - EIPs - Fellowship of Ethereum Magicians
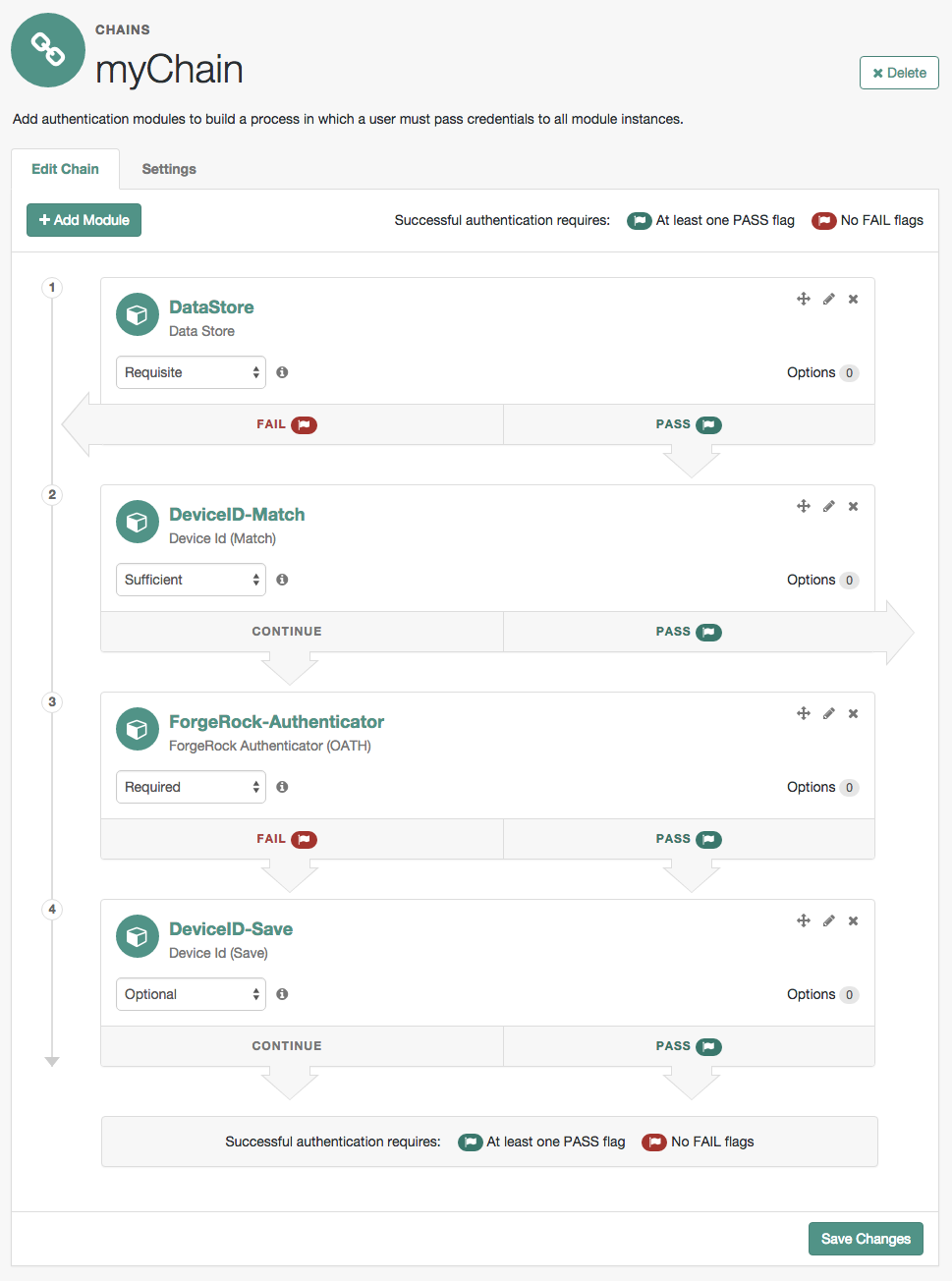
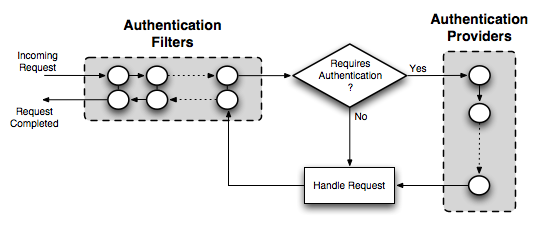
ForgeRock Access Management 7.0.2 > Authentication and Single Sign-On Guide > Authentication Modules and Chains